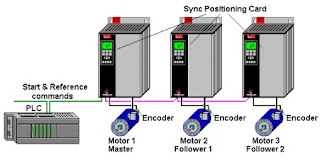
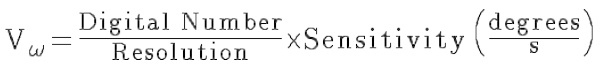For reasons of efficiency, maintence, and economics, data acquisition and control platforms have migrated from isolated in-plant netwoeks using proprietary protocols, and the internet. The downside of this transition has been to expose SCADA systems to the same vulnerabilities and threats that plague Windows-based PCs and their associated networks. Some typical attacks that might be mounted against SCADA systems that employ standard hardware and software are listed here: Image Saurce: gcn.com - Malicious code such as viruses, trojan horses, and worms - Unauthorized disclosure of critical data - Unauthorized modification and manipulation of critical data - Denial of service - Unauthorized access to audit logs and modification of audit logs Terminology of PLCs The L3GD203-Axis Gyro Introduction To Robotics Classification Of Robotics SCADA System Architecture Most SCADA system, paticularly the local PLCs or controllers, have ro operate in real-time or near re...